Cloud computing has set the stage on fire with its incredible features including scalability, agility, minimized physical infrastructure, and cost savings. However, with the increasing amount of data and other critical applications moving to the Cloud, it has become quite challenging to maintain a secure Cloud environment. Gartner’s forecast on global end-user expenses for risk management and security is expected to touch $215 billion in 2024, indicating a 14.3% rise from the previous year.
With cyberattacks looming large, your organization’s reputation may be at stake due to financial losses, data theft, and more. This implies that even a single breach can spell disaster. Research indicates that only 4% of the organizations maintain sufficient security for their Cloud-based resources. In 2023, about 80% of the breaches reported compromised data stored in Cloud.
The Significance of Cloud Security in Today’s Digital Setting
With the advancement in technology, enterprises are increasingly adopting the Cloud security practices to manage the mounting cyber threats effectively. In the current digital scenario, securing infrastructure and data storage has become imperative for organizations to counter the risks involved in third party Internet exposure. An important point to remember to enhance Cloud security is to ensure that the devices and users are well-connected to the Cloud apps.
What is Cloud Security?
Cloud security secures applications, client sources, architecture, and infrastructure stored in Cloud platforms from the cyber threats. The primary objective is to protect these assets from digital threats, unauthorized access, and data breaches, warranting that they are safe and well-protected.
Here are some of the best Cloud Security practices for 2024 and beyond:
Implementing Multi-Factor Authentication (MFA)
As businesses are increasingly migrating their operations to Amazon Web Services (AWS) Cloud, it is critical to ensure vigorous security measures to protect sensitive data. Implementing multi-factor authentication is a significant step to prevent unlawful access and cyberattacks.
MFA acts as a critical shield and improves the security of the user accounts available within the AWS system. Implementing MFA enhances the security for banks and other financial institutions, making it difficult for unauthorized users to gain access to sensitive information and assets. In addition, MFA streamlines the tracking as well as management of user access, as every user needs to have his/her unique pick of authentication factors.
AWS provides different MFA options to strengthen security measures such as FIDO Security Keys, Virtual MFA Devices, and Hardware TOTP Tokens. Technologies such as Artificial Intelligence and Machine Learning are also increasingly used in MFA for analyzing user behavior, evaluating risk scores, and more.
Employing Strong Encryption Protocols
Encryption is one of the important pillars that facilitates a secured experience in Cloud. Over years, encryption has become a gold standard for privacy assurance and data protection policies globally. Though encryption plays an important role in the Cloud landscape, only a few organizations get the encryption strategies in the right manner. Encryption should be regarded as a strategic security goal of your enterprise, rather than considering it as a desired feature provided by the Cloud vendors.
The encryption process does not imply just a set of principles that you can apply to the entire data. There must be a definite plan for encrypting data in its two different states – ‘Data at Rest’ and ‘Data in Transit’. The former is about promoting a secured data setting by establishing access controls, using metadata instead of raw data, and more. The latter implies safeguarding data transit pathways by administering robust encryption protocols including SSL and HTTPS, and leveraging encryption tunnels.
Safeguarding Your Endpoints
Endpoints such as mobile devices, desktops, tablets, and laptops act as a gateway for the users to connect with Cloud apps and data. As these resources are directly associated with Cloud, it is mandatory to safeguard them to prevent data breaches, unauthorized access, and other security issues. Analyze and upgrade the endpoint security practices regularly to reduce risks and secure the Cloud-based data. To accomplish this, formulate a comprehensive security plan which includes anti-malware, firewalls, and access control, to name a few. Given the complicated nature of endpoint security, tools like endpoint protection platform (EPP) and endpoint detection and response (EDR) can help strengthen your security. Additional options to consider are VPNs, patch management, insider threat prevention, etc.
Providing Training for Your Employees
Employee training involves educating the employees about the cybersecurity standards. Providing adequate training helps to safeguard sensitive data and prevent unauthorized access by identifying and countering threats in a timely manner. The training programs should focus on IT risks which involve usage of unauthorized tools that compromises security and data integrity. The topics should necessarily include setting up strong passwords, recognizing potential threats, spotting social engineering attacks, and so on. Further, ensure that the security personnel are well-aware of the emerging risks and mitigation measures. Encouraging accountability is strongly recommended through regular discussions, establishing security standards, effective password management, and more.
Understanding the Shared Responsibility Model
The shared responsibility model refers to the security responsibilities offered to the Cloud providers and customers. The provider safeguards the Cloud network, whereas the customer secures the applications, data, and configurations. This framework enables businesses to manage Cloud security effectively and minimize risks by elaborating on responsibilities and complying with security policies. Several PaaS and IaaS providers offer detailed documentation to define roles in different deployment situations. While checking on Cloud vendors, evaluate the security roles to avoid miscommunication which may lead to serious lapses in security.
Here is a shared responsibility model by AWS:
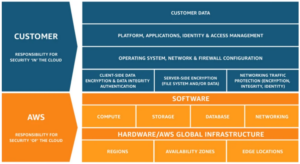
Source: 11 Cloud Security Best Practices & Tips in 2024 (esecurityplanet.com)
Incorporating Additional Cloud Security Solutions
Integrating supplementary Cloud security solutions such as integrity detection and prevention system (IDPS), cloud access security broker (CASB), and identity and access management (IAM), improves the security layers and provide a stronger protection against cyberthreats and potential attacks in Cloud networks. Popular IAM solutions include JumpCloud, Okta Workforce Identity, OneLogin, etc.
Wrapping Up
Cloud security tools are a must-have in the modern digital world, as they safeguard you from the potential threats and cyberattacks. A Cloud infrastructure requires many layers of defense, and hence it is imperative to adopt the best Cloud security practices to protect your data and secure your business. Read this blog and have a glimpse of the top Cloud security practices that will help you secure your assets efficiently in your journey forward.
We offer a wide array of Cloud solutions for our clientele, which enables them to stay on the competitive edge. If you have any questions regarding our services, don’t hesitate to contact us at itsolutions@milestone.tech.




